North Korean government-based hacking groups continue to exploit remote code execution vulnerabilities in Chrome, as Google security teams work to counter-threat. According to reports on February 10th 2022, Google’s Threat Analysis Group (TAG) made discoveries of the threat and began tracing/tracking the threat which was publically known as “Operation Dream Job” and “Operation AppleJeus“.
In a blog post from Google’s internal team, Google stated that they observed a sophisticated campaign “…targeting U.S. based organizations spanning news media, IT, cryptocurrency and fintech industries.” These industries while according to Google most appeared to be in the United States, Clear Sky Cyber Security (a global cyber security vendor) stated that this is a widespread campaign.
Operation Dream Job Campaign
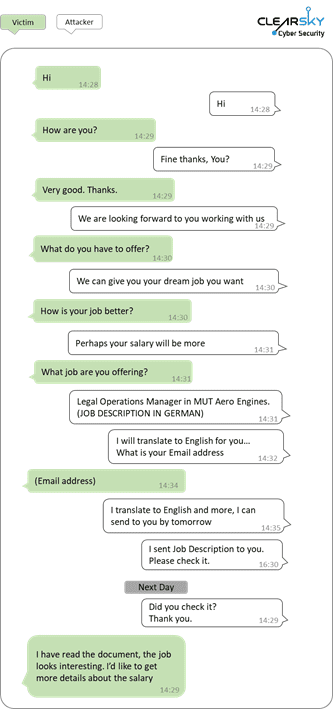
In the case of this campaign, this campaign focused on defence and governmental organizations and specific employees of those types of industries. Attributed to the “Lazarus group” of hackers, the campaign was successful in infecting several dozen companies and organizations in Israel and globally.
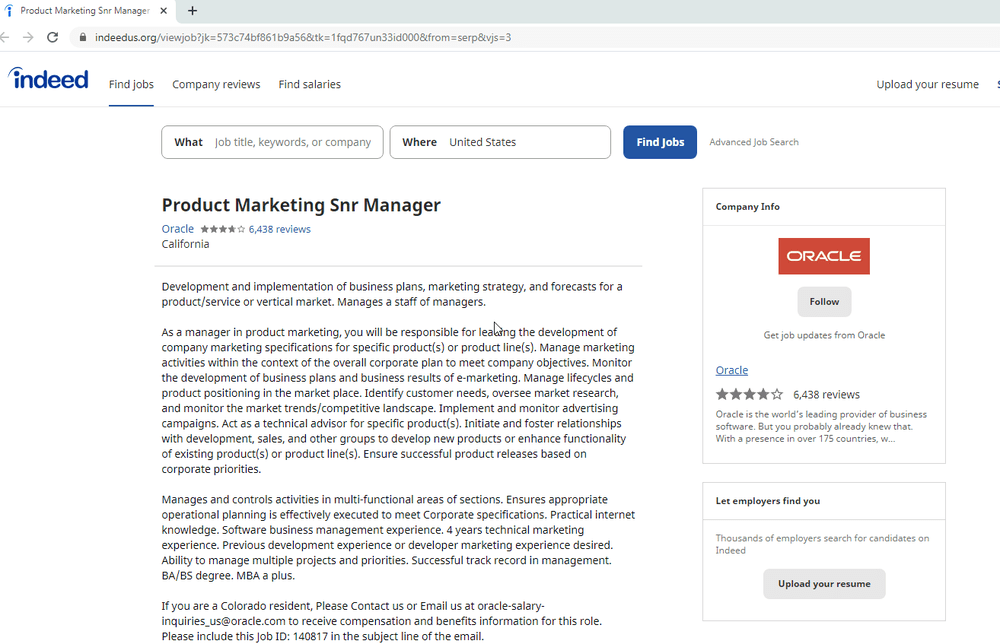
The North Korean campaign, “Lazarus” group (aka HIDDEN COBRA), succeeded in targeting individuals in targeted organizations with the prospect of their “dream job.” According to ClearSky, targets were lured with the prospect of a job with “…some of the most prominent defence and aerospace companies in the US, including Boeing, McDonnell Douglas, and BAE.” Then once organizations were infected, the attackers collected intelligence regarding the company’s financial and other affairs in an attempt to extract money.
What was most interesting in this campaign was the extent to which hackers went to extract information and engage with their targets to facilitate the attack. In the image below, which was an extract from ClearSky Sec’s website, an attacker used WhatsApp messages to communicate with the target and share documents.
Operation AppleJeus
A slightly different angle, but attributed to the same “Lazarus group” of North Korean state hackers, was a fake installer with macOS malware. According to SecureList from Kaspersky Labs, the goal of the “AppleJeus” operation was specifically to extract money from Cryptocurrency exchanges with the help of malicious trading software.
In this platform-agnostic attack, hackers supposedly went “the extra mile” in developing software for both the Windows and macOS platforms. By developing for both platforms, hackers were unusually able to deploy aggressively across devices if/when users downloaded their software
Kaspersky stated that they first discovered the vulnerability when they were investigating a cryptocurrency exchange that has already been attacked by Lazarus Group:
“While investigating a cryptocurrency exchange attacked by Lazarus, we made an unexpected discovery. The victim had been infected with the help of a trojanized cryptocurrency trading application, which had been recommended to the company over email. It turned out that an unsuspecting employee of the company had willingly downloaded a third-party application from a legitimate-looking website and their computer had been infected with malware known as Fallchill, an old tool that Lazarus has recently switched back to. There have been multiple reports on the reappearance of Fallchill, including one from US-CERT.” – Kaspersky
While this is certainly not going to be the last we seek of hacking groups like Lazarus Group, Kaspersky stated that this vulnerability should serve as a “wake-up call” to non-Windows users.
How to defend against the threat?
As the threat from online hacking groups online continues to evolve, it’s now more than ever important to ensure good online hygiene and ensure your security is up to date. In the Chrome browser, Google has enabled a new feature in Chrome Called “Enhanced Safe Browsing“. This feature protects Chrome users by displaying warnings before accessing potentially harmful links and apps.
Secondly, use a good anti-virus and online protection suites like Microsoft Defender or F-Secure SAFE. These tools can reduce and prevent exposure to unruly software online and reduce your attack surface to all kinds of threats. As always keep up to date with any updates from our team here.
Images above from ClearSky Sec and Google TAG






















Comments